
What Is an Anti-Detect Browser? A Complete Guide to Its Use in Web Marketing
Use an anti-detect browser to avoid website tracking and securely manage multiple accounts. Learn how it works, why it's essential for ad management and marketing, compare top tools, and discover advanced uses with SMS verification.
2025-08-140 minute readTips
Share
What are Anti-Detect Browsers?
Anti-detect browsers are specialized browsers that, unlike common browsers like Google Chrome or Firefox, can freely modify and spoof the "browser fingerprints" sent to websites.
*For more information about browser fingerprints, please refer to our article here.
Simply put, browser fingerprint information is a collection of data consisting of various elements related to the user's device and environment, which helps website operators uniquely identify users.
For example, this includes OS type, browser version, installed fonts, screen resolution, GPU information, timezone, language settings, and more. In normal settings, this information is automatically included and transmitted in browser communications, so even if you are not logged into a website, it can serve as a clue to identify that a series of accesses belongs to one specific person.
However, using anti-detect browsers makes it possible to replace this information with different (random or arbitrary) values. As a result, even when the same person is accessing, it becomes easier for the service side to recognize them as "different users."
Typical anti-detect browsers enable access disguised as "fictional specific individuals" by registering large quantities of such random browser fingerprints as presets.
Background of Anti-Detect Browser Usage Expansion

One factor behind the expansion of anti-detect browser usage is the recent advancement in web service security.
Until a few years ago, it was somewhat possible to manage multiple accounts or bypass regional restrictions simply by using VPN or proxies to change IP addresses. However, currently, multi-faceted identification technologies have been introduced beyond IP addresses, including browser fingerprints, cookies, local storage, WebRTC leak information, and more.
Particularly, major platforms like Google, Meta, and TikTok perform extremely precise device authentication to prevent fraudulent use of advertising accounts and social media accounts. As a result, "changing only the IP" is no longer sufficient, and the need to customize and spoof the entire device environment has increased. Anti-detect browsers can be said to be tools specifically designed to respond to this new detection environment.
Application Areas and Use Cases of Anti-Detect Browsers
 A typical example where anti-detect browsers are utilized is web marketing, including advertising operations.
A typical example where anti-detect browsers are utilized is web marketing, including advertising operations.
As an example of anti-detect browser utilization, their use in market research or competitive analysis, where different personas are used to explore information, would be easy to understand. Various virtual users are constructed with different regions, genders, and interests in mind, enabling the deployment of advanced intelligence activities such as completely exposing competitors' advertising strategies.
Furthermore, anti-detect browsers are often used in fields that require high anonymity or independence (which may include questionable cases). In other words, the scope of anti-detect browser utilization far exceeds the realm of general marketing and functions as a powerful tactical tool for artificially creating "influence" and "profit" itself in digital space and overcoming all constraints.
For example, in today's reputation economy, reviews and engagement have enormous value. Many of you may have used reviews from sites like Google Maps, The Fork, and TripAdvisor as criteria for decision-making. Users of anti-detect browsers have succeeded in building reputation organizationally and artificially by intentionally manipulating ratings of specific products in such review markets, marketplaces, and app stores, creating fake enthusiasm and guiding public opinion in specific directions. (Because this is highly sophisticated, in most cases it is not detected by automatic spam removal tools, etc. Therefore, platforms that are helpless against these reviews need manual responses.)
Also, in the world of web advertising, budget or audience reach limitations imposed by platforms are effectively neutralized by preparing countless "alternative personas." This may allow for immediately replacing blocked accounts and continuing campaigns (although it should be noted that this is explicitly prohibited by many advertising networks).
Key Features of Anti-Detect Browsers
The strength of anti-detect browsers is concentrated in advanced feature sets for creating extremely sophisticated digital "alternative personas", not just anonymization tools. The core of this is the trinity of functions: "browser fingerprint spoofing," "complete profile separation and management," and "strategic IP address allocation." By working together, these enable one user to behave as if they were countless different people scattered around the world.
1. Complete Browser Fingerprint Spoofing
Websites collect vast amounts of information sent from browsers to identify who you are. This is called "browser fingerprinting" and is brought about not just by OS or browser type, but by combinations of very diverse elements. For example, the following can be included:
Hardware Information (Canvas/WebGL Fingerprint): Depending on the type of computer graphics card and drivers, slight differences occur in pixel-level "bleeding" or "quirks" when browsers render graphics. Anti-detect browsers intentionally add different noise to these slight rendering results, making hardware-level identification completely impossible.
Environment Information (fonts, timezone, language settings): The types of fonts installed on a computer and the combination of timezone and language settings can be unique identifiers more than you think. For example, just the combination of "English Windows environment with many special Chinese fonts for design installed" can narrow down individuals from users worldwide with considerable accuracy. Anti-detect browsers optimize this information for each profile. For example, for a profile of "male Mac user living in Los Angeles," they perform meticulous spoofing such as returning only Pacific Standard Time (PST), English settings, and the font group standard in macOS.
This allows a "Windows user from New York" to impersonate a "Mac user from London" or an "Android user from Singapore" with the click of a button.
2. Profile Management and Data Separation
Next important is the profile management function that completely separates the activity history of each "alternative persona." While regular browsers (e.g., Google Chrome) also have profile functions, these are merely simple separations for convenience. On the other hand, anti-detect browser profiles function as "containerized" independent browser environments.
Specifically, data such as cookies, session information, browsing history, and cache saved in one profile are completely isolated from other profiles. For example, even if you log into an e-commerce site in Profile A and browse products, when you open the same e-commerce site in Profile B, you will be treated as a completely new visitor. Login information will not be carried over, and even recommended ads based on browsing history will not be displayed.
Such "complete separation" demonstrates enormous effectiveness when using multiple accounts. Since it can completely shut out the biggest risk factor for platforms suspecting that "one person is using multiple accounts" (e.g., cookie mixing), it enables safe account management.
3. Strategic IP Address Usage (Proxy Management)
Even if you spoof "devices" with fingerprints and "user activities" with profiles, if all access source IP addresses are the same, being the same person will be immediately exposed. Therefore, proxy management that assigns different IP addresses to each profile becomes essential.
Anti-detect browsers can set individual proxy servers for each profile.
And particularly important are the types of proxies that can be used.
- Residential Proxy: These are IP addresses connected to exactly the same internet lines as general households. They are almost never considered mechanical access and can impersonate "general users" with very high reliability.
- Mobile Proxy: These are IP addresses from mobile carrier networks. On platforms like social media where smartphone access is central, they are recognized as extremely natural users.
By combining these proxies, it becomes possible to design perfect alternative personas including physical location information, such as "Profile A with residential IP from New York" and "Profile B with mobile IP from Paris."
By organically combining these three functions, anti-detect browsers function not just as tools, but as "platforms for reproducing completely different people's digital environments."
Risks and Precautions
 Thus, while anti-detect browsers may be considered for deployment in marketing that stays one step ahead of competitors, caution is also necessary in their use.
Thus, while anti-detect browsers may be considered for deployment in marketing that stays one step ahead of competitors, caution is also necessary in their use.
First, it is necessary to note that in some services, such "identity spoofing" may be explicitly prohibited in terms of service. In other words, environment spoofing itself may lead to terms violations or legal problems. Also, if settings are incorrect, there is a risk of being detected as an "unnatural environment" instead, causing accounts to be suspended faster than usual. For example, using old browser versions in the latest Windows environment or having impossible combinations of resolution or language settings makes detection systems more likely to recognize this as "abnormal."
Furthermore, since anti-detect browsers are powerful tools, if misused, they can be used for crimes such as fraud or unauthorized access, and should only be used for lawful and legitimate purposes. When using them, it is important to clarify the purpose and strive for safe and appropriate settings and operations.
With these risks in mind, the next section will introduce several typical anti-detect browsers.
Representative Anti-Detect Browsers
Among representative anti-detect browsers, we introduce 5 products that support cryptocurrency payments and are particularly well-known.
It is recommended to determine which product to choose by checking the fulfillment rate for your own needs, such as price per profile or availability of free trials.
- Dolphin {Anty}
- Free trial: Available (10 profile limit)
- Price: 10USD/60 profiles/mo~
- Developer: Zhitnyakov software (Cyprus)
A free plan without time restrictions is available, and Dolphin {Anty} is the most recommended browser for first-time users to understand "what is an anti-detect browser?"
After grasping usability and transitioning to paid plans, it also offers flexible pricing, with a fixed $10 providing 60 profiles, and every additional $10 spent unlocking 10 more profile areas.
- Multilogin
- Free trial: 1.99EUR / 3-day trial available
- Minimum price: 9EUR/10 profiles/mo~
- 1GB/mo residential proxy bandwidth provided
- Developer: Multilogin Software OÜ (Estonia)
This is the oldest browser that has been used in the industry for the longest time. Advanced fingerprint spoofing technology and robust profile management functions backed by years of track record have gained enormous trust, especially from professionals who require large-scale advertising operations or strict account management.
Residential proxies are built-in, which is convenient when you want to start with minimal configuration.
- GoLogin
- Free trial: 7 days (paid plans have 14-day money-back guarantee)
- Price: 24USD/100 profiles/mo~
- 2GB/mo residential proxy bandwidth provided
- Developer: GOLOGIN LLC (USA)
A browser with attractive relatively reasonable pricing. Since basic fingerprint customization and profile separation functions can be used with simple operations, it is popular as an option when individuals or small teams introduce anti-detect browsers.
- Kameleo
- Free trial: Available (300-minute time limit)
- Price: 45EUR/Unlimited profiles, 10 Concurrent browsers/mo~
- Developer: Outis Nemo Ltd (Hungary)
Characterized by a clear and intuitive user interface. It supports spoofing not only Windows and Mac profiles but also Android profiles, and is known as a tool that even beginners can handle easily for a wide range of applications. Unlike Dolphin {Anty}, Multilogin, and GoLogin introduced so far, there is no limit on the number of profiles that can be saved, and a major feature is that pricing varies according to the number of profiles that can be launched simultaneously.
- Undetectable
- Free trial: Available (browser fingerprint spoofing only possible)
- Price: 49USD/Unlimited profiles(Local storage)/mo~
- Developer: MOBICO SERVICES LTD (Cyprus)
Undetectable is the choice with the best cost performance among products offering unlimited profile storage. The $49 plan provides only 25 types of browser fingerprints, and if you want more, additional purchases of $1 each are required, but it is an excellent choice when seeking cost performance.
Utilizing Disposable Phone Numbers
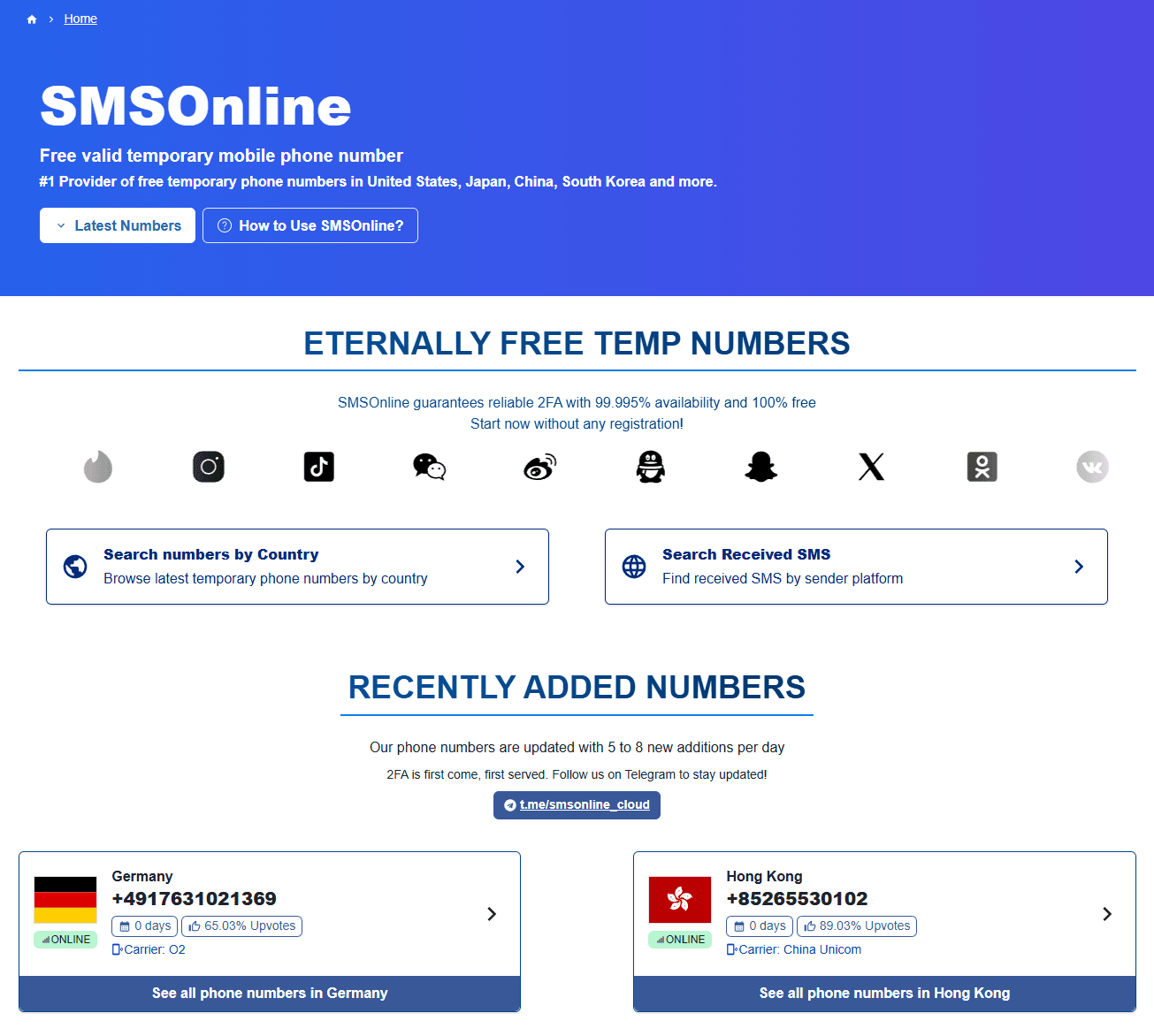
SMSOnline
While we'd like to think that creating independent identities using anti-detect browsers is complete, it's actually not that simple. In many web services, when creating multiple accounts, using phone numbers biased toward specific carriers or regions can become a factor in spam detection or account suspension.
To avoid this problem, using disposable phone number services like SMSOnline and utilizing phone numbers from various countries in rotation is effective.
This is a revolutionary service that allows sharing phone numbers with users worldwide on the web. Phone numbers from over 40 countries are available for free, with 5-7 added daily.
It's possible to access free phone numbers without any hassle of account registration or credit card registration.
Usage is very simple:
- Access SMSOnline.
- Select the country you want to use from over 40 countries worldwide.
- Choose an active phone number from the displayed list. It's recommended to use new phone numbers since old ones may already be used by many services.
- Enter our phone number into the website or service where you want to authenticate, just like normal SMS authentication.
- Just wait for the OTP to be temporarily published on the website. It won't take more than a few minutes!
We prioritize security and have a system where only the latest 15 OTPs are displayed. Usually, OTPs disappear from logs and become unviewable in about 2-4 minutes, so there's no worry about information remaining for long periods. This allows rapid OTP confirmation when needed while minimizing subsequent information leak risks.
Currently, SMSOnline provides available phone numbers in over 40 countries including China, USA, Sweden, Hong Kong, and Taiwan. Our service is already used by millions of users monthly, but through high-pace phone number updates, we provide equal access to disposable phone numbers for all users.
Also, since this service is mainly operated through advertising revenue, users can enjoy these services without paying any fees.
Introducing SMSOnline Premium
High Security and a Large Stock of Numbers
SMSOnline Premium is a premium service designed for users who need more secure and abundant phone numbers. Unlike the free version, numbers in the Premium service are never shared, ensuring complete privacy and a safer environment.
Currently, it connects to hundreds of thousands of numbers in over 40 countries, meeting demands whether you need a specific country's number or a large batch at once. Pricing starts at just a few cents per message, keeping costs low.
Flexible Payments and a Reliable Refund Policy
We prioritize convenience by supporting a wide range of payment options. For privacy-focused users, anonymous cryptocurrencies like XMR and DASH are accepted. We also support USDT, BTC, and other major cryptos.
For fast transactions, we accept VISA, MasterCard, AMEX, UnionPay,MIR card, as well as Alipay, Google Pay, Apple Pay, and more.
Not satisfied? No problem. If you meet our conditions, we offer a 100% refund guarantee, letting you try the service risk-free. Experience the power and security of SMSOnline Premium today!
Sign up here and get 10% off your first balance purchase.
DISCLAIMER: While our service provides high anonymity to customers, please ensure that your usage method does not violate local laws in your country of residence and the country where the authentication service is located, as well as the terms of service of the authentication service. Our service is premised on use for development and testing purposes, and usage that violates these conditions is not permitted. We are located in Romania and operate based on Romanian law and EU law.
